Background, First Impressions and BLE
As a tech enthusiast, I am always on the lookout for interesting gadgets and devices. One day, while browsing through eBay, I stumbled upon a listing for a brand new Dsoon H8WIFI WiFi/Bluetooth connected trail camera for just $20. Despite its low price, the device appeared to be in new condition and had all the features I figured I could use for some interesting projects. I hopped on it and hit the “Buy It Now” button then eagerly awaited its arrival.
Upon receiving the trail camera, early inspection definitely concluded the unit was brand new with protective covers and all.


It seemed to be built relatively well and seemed like it would last a long time out in the elements as it would be intended to be used. However, as I read through the manual I had a feeling it was not going to be exactly what I had hoped for. The manual had a section that said, “The Trail Cam’s wifi can not hook to the internet, it is not a webcam or cellular camera.”. It then went on to explain that the device basically acts as its own wifi AP and that wifi is disabled by default to save battery usage and is enabled by through always on Bluetooth connection. Then I saw the words, “only works with the ‘Trail Cam Pro’ App”. As being on-par with run-of-the-mill, overseas mass produced electronics, I cannot say I was exactly surprised, but I was a bit disappointed, although intrigued at the same time. I figured based on the reviews I came across I was going to be in for an interesting experience as with most of these types of products and their mobile apps.
I begin my first adventure to even find the app, the one mentioned in the manual did not seem to exist in the app store, so the next thing I did was check the manufacturer’s name “Dsoon” this turned up a few matches. I went ahead and downloaded the one that had the most reviews / downloads and hoped for the best.
Upon getting the app installed I was greeted with what you could call a very “clunky” and “awkward” experience.. As the manual had stated, the app would basically connect to the trail cam over bluetooth, send a command, then open the android interface to connect to a wifi network for you to select the matching device AP. After connecting, the app seemed to crash. Then upon reopening, it would present you with a rudamentry interface to edit settings, download files, or live stream the camera’s video. It was at this point that I knew was going to have to figure out how all of this communication was working to get the user experience that I wanted with the device.
Thus began my journey to reverse engineer the bluetooth and wifi communication..
First task was to tackle the Bluetooth.
This was accomplished with using Android’s built-in Bluetooth packet capture feature. With my Android tablet set to “developer mode” I was able to capture the bluetooth packets by:
- Go to Settings.
- If developer options is not enabled, enable it now.
- Go into developer options.
- Enable the option Enable Bluetooth HCI snoop log.
- Enable the Bluetooth option and Connected to the device.
- Perform the actions which need to be captured.
- Turn off the Bluetooth on the device.
Next challenge, getting the bluetooth packet capture off of the device there are a number of ways to accomplish this, but I used ADB. It was a bit tricky to chase down the path, and apparently depending on the brand and android version this differs, but once traced down using ADB commands:
- To find the log file name.
adb shell cat /etc/bluetooth/bt_stack.conf
- Then pulled the file using:
adb pull /data/log/bt/btsnoop_hci.log
With various different ways to get the file.
Once I had the file I could start digging through the data with Wireshark.
Since I was only looking for the “write” command I filtered the packets and found exactly what I was looking for:
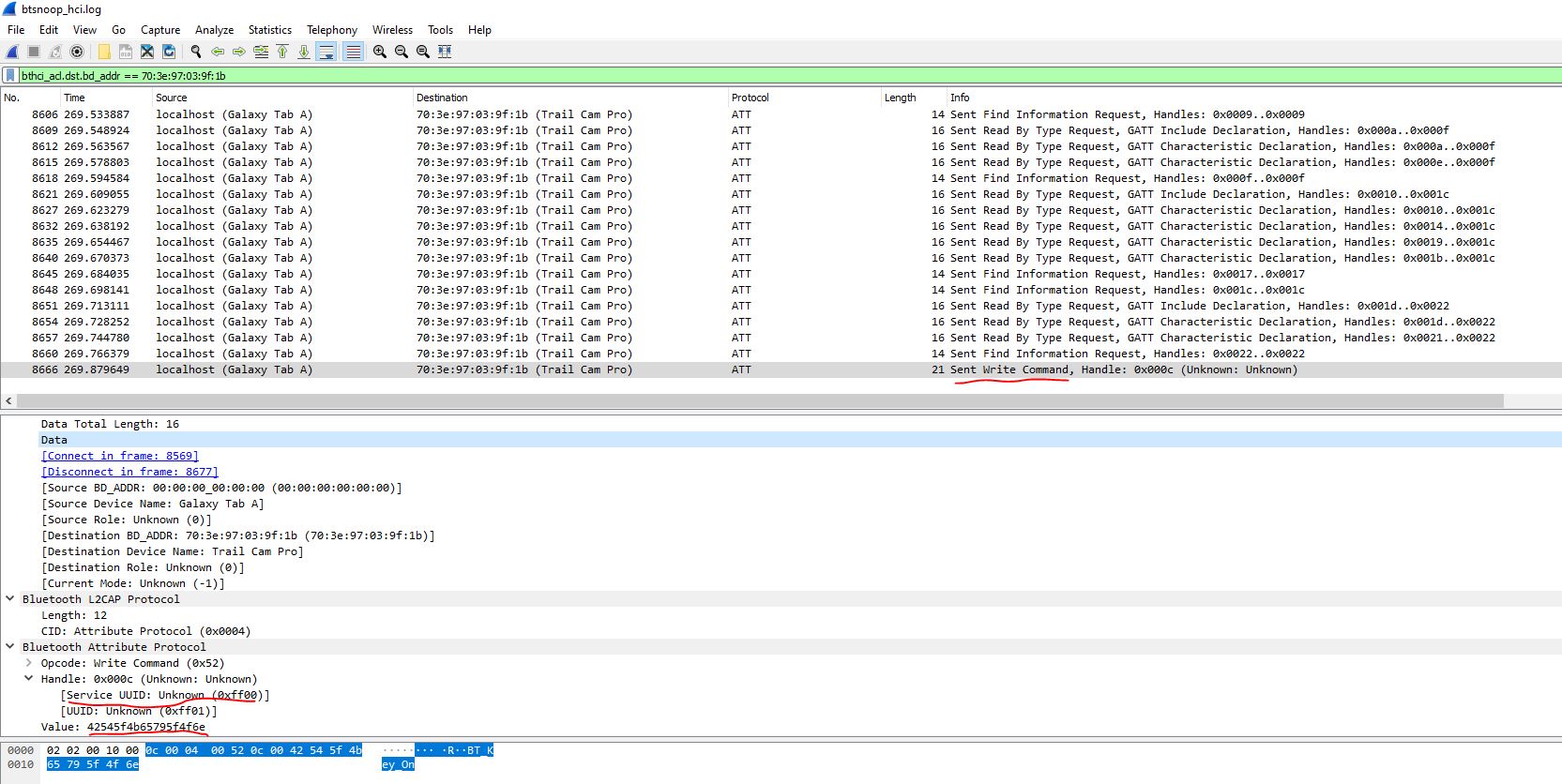
As you can see we get the target Bluetooth Attribute Protocol details:
Service UUID: "Unknown (0xff00)"
UUID: "Unknown (0xff01)"
Value: "42545f4b65795f4f6e" or 'BT_KEY_ON'
Next I needed to validate the command worked. To accomplish this I downloaded the nRF Connect App to my Android Phone which allowed me to connect to the device and send raw data to the desired target UUID’s.
Example of using that app:
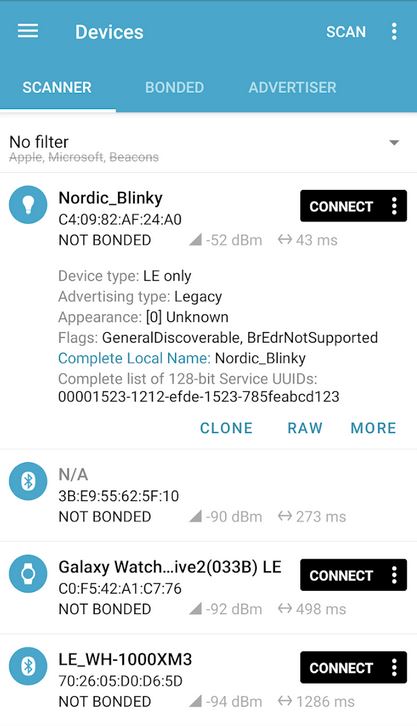
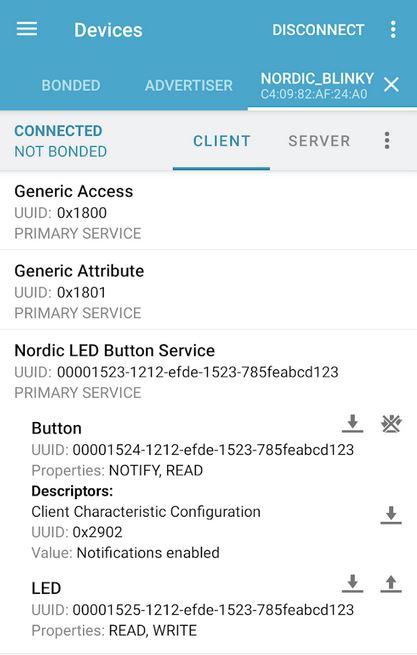
As soon as the above command ‘BT_KEY_ON’ is sent to the target UUID’s the Trail Cam would click indicating a reset, and the wifi AP came up.
Next task was to reverse engineer the network communication. I will continue that in part 2 of the Wifi/BLE Trail Cam investigation..
1 thought on “Wifi BLE Trailcam Investigation Part 1”